On march 10 2020 a security vulnerability was published for Remote Desktop Connection Manager (RDCMan). At the same time Microsoft removed the download from their site pushing people towards the use of MSTSC or Universal Remote Desktop client. If you like having multiple connections with group based inheritance (as RDCMan does), you’re out of luck with those alternatives.
The security vulnerabilty in RDCMan isn’t all that bad actually. You need to open a .RDG file that was modified by an attacker which could then expose data via an XML external entity attack.
Since most of us use a local .RDG configuration file this sort of attack is pointless as someone who can modify that file already has access to the filesystem.
That being said; If you want to use RDCMan but can’t because of the vulnerability then you still have the option to fix the issue yourself.
In .NET applications this can be achieved by setting the XmlResolver on the XmlDocument type to null.
Luckily RDCMan was written in .NET which makes it rather easy to make this modification with a tool like dnSpy
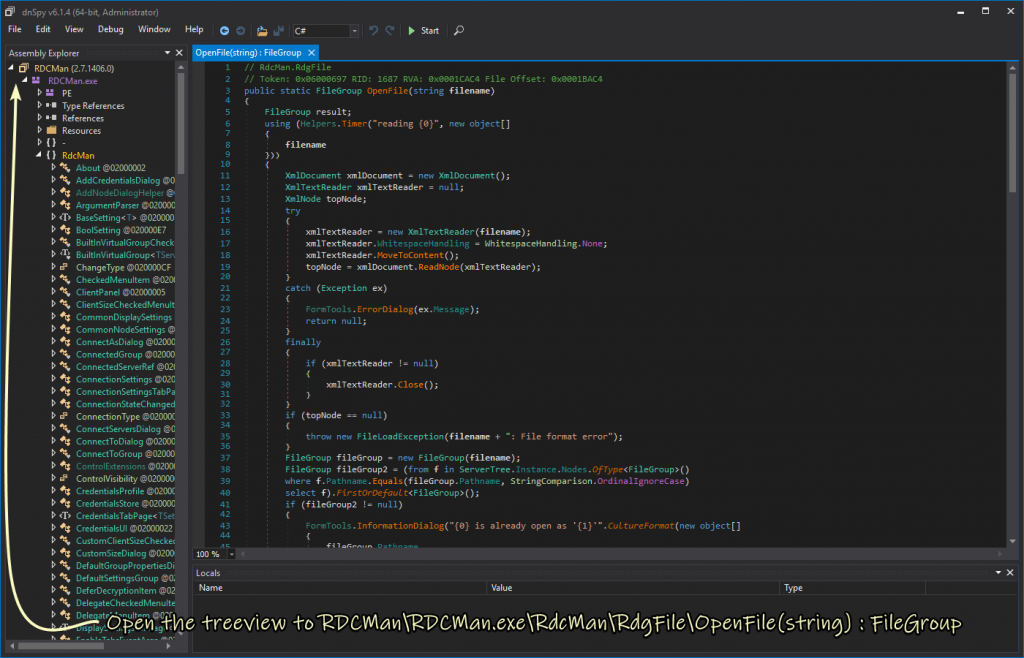
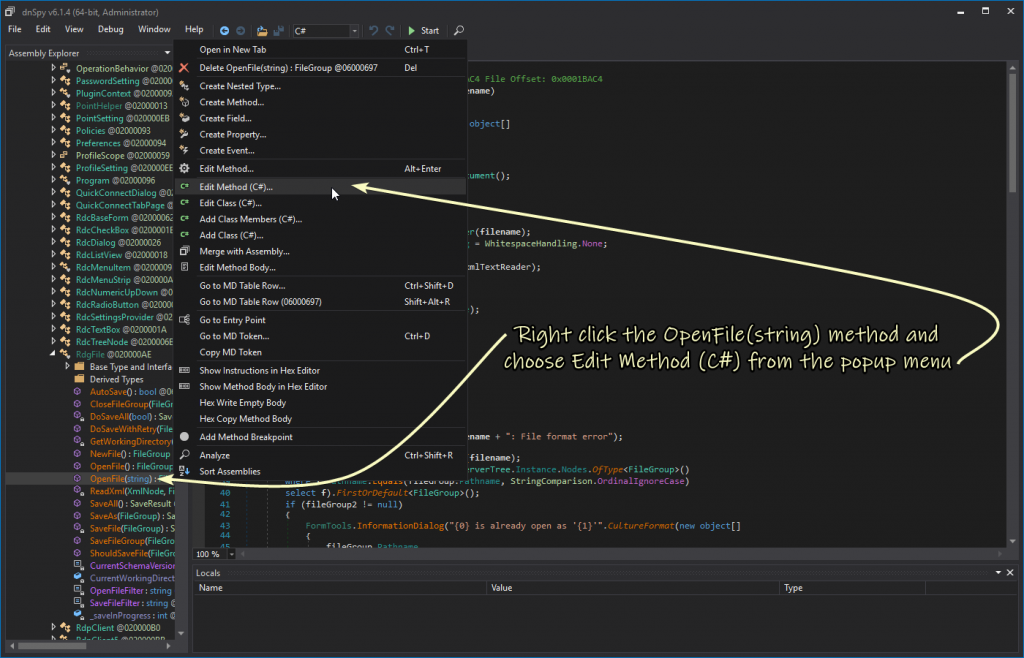
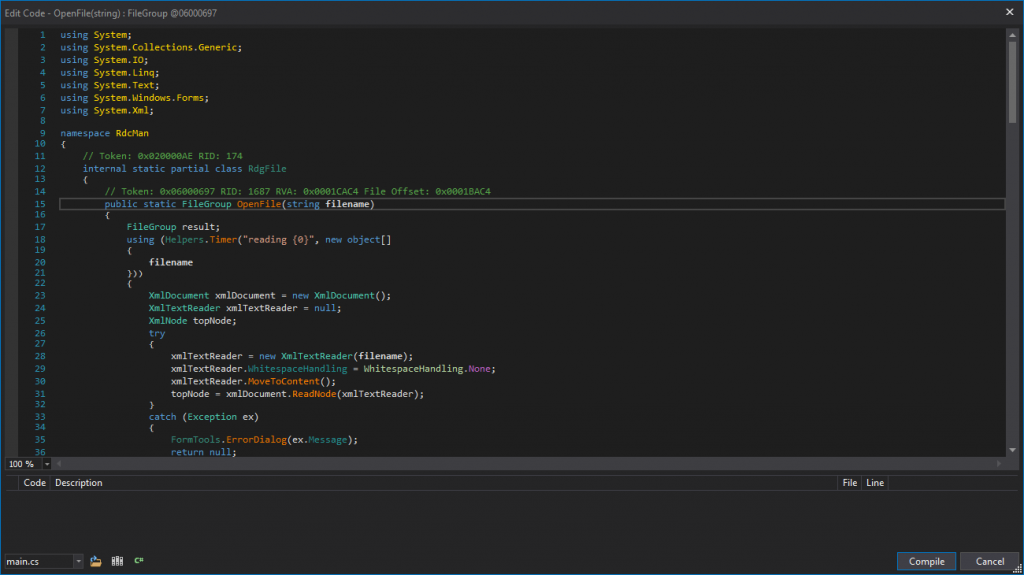
And make the following changes
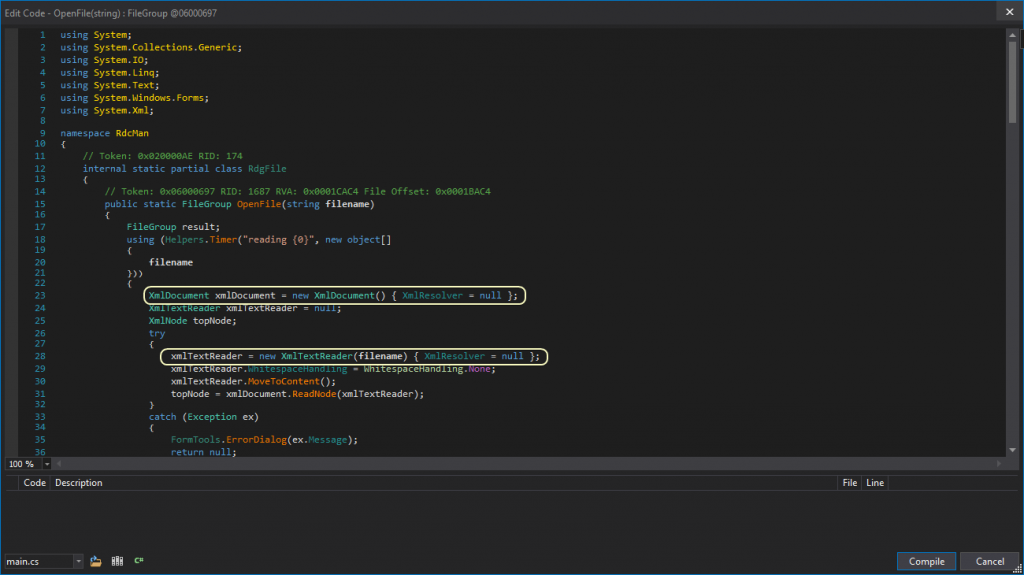
After adding the two XmlResolvers hit the Compile button. After which the changes should show up in the main window of dnSpy.
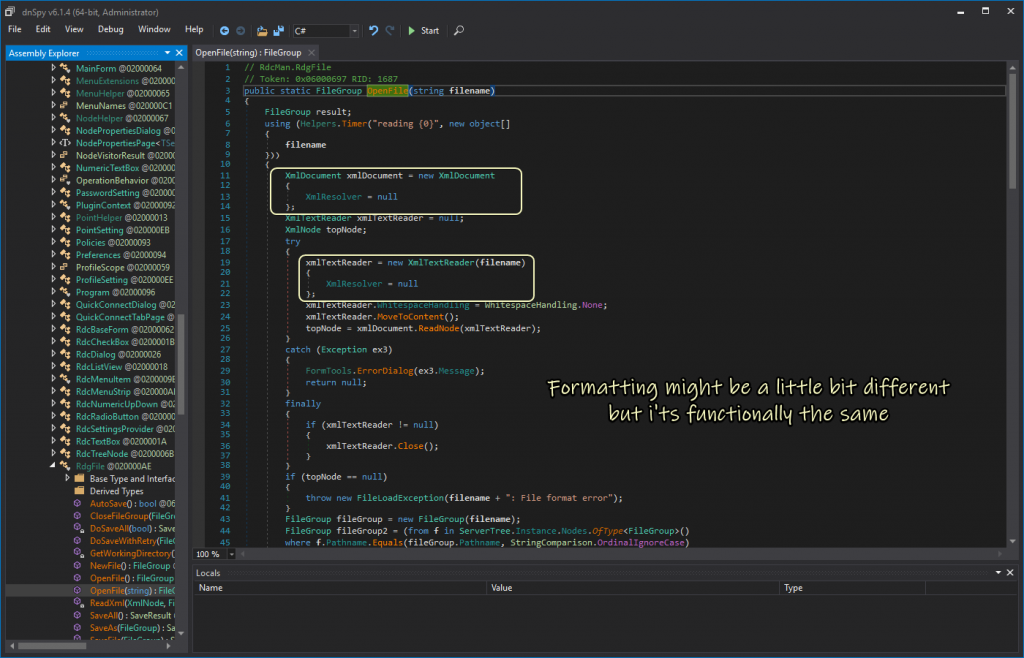
Now we just need to save the changes to RDCMan.exe
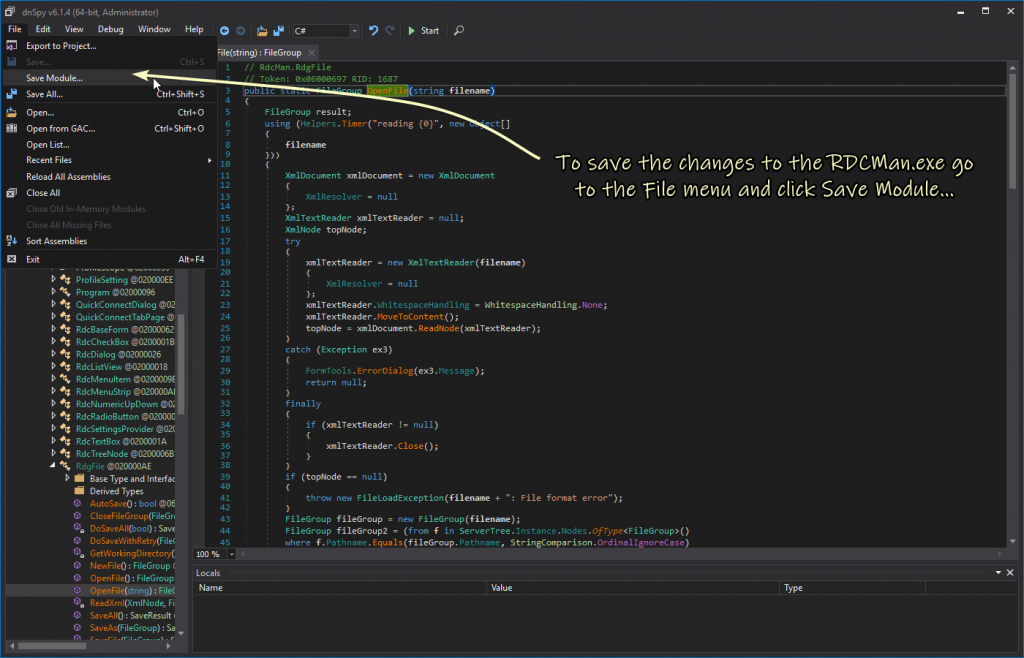
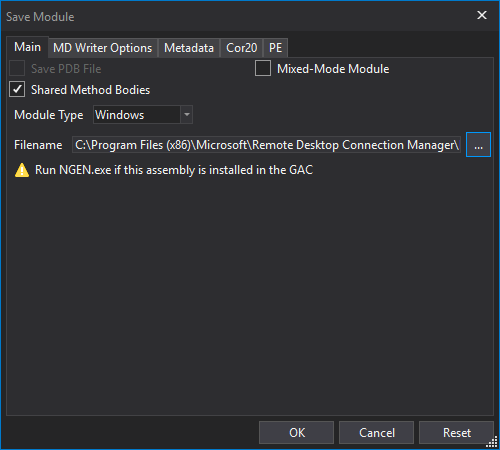
Thats it, you should* (see note 4) now have a CVE-2020-0765 patched RDCMan.exe
Some notes:
1) You should still be on the lookout for a RDCMan alternative as this software is no longer maintained and might possibly no longer work with newer versions of RDP or new exploits could emerge.
2) This modification is purely for educational purposes, just to see if it could be done easily.
3) Do this at your own risk, no guarantee is given.
4) It’s a theoretical patch; No testing with a malicious RDG file was done.
5) Although the Remote Desktop Connection Manager dowload was removed from the Microsoft site, The Wayback Machine still has it.